Configure SAML single sign-on for portal-only customers with Entra ID (formerly known as Azure AD)
Introduction
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, such as an identity provider and a service provider.
SAML for single sign-on (SSO) allows customers to authenticate through the organisation's Identity Provider (IDP) when logging in to the Jira Service Management Customer Portal. During an active session, customers only need to log in once to access multiple portals for one Jira Service Management instance.
Customers outside the organisation can only access the organisation's Jira Service Management portal. Atlassian does not count these customers toward the Atlassian Guard subscription billing. Learn more about Jira Service Management customer accounts.
Pre-requisites
To configure SSO for JSM Portal-only customers, you need:
- Jira Service Management Portal
- Atlassian Guard Subscription
To configure SSO for JSM Portal-only customers, you need below roles:
- Organisation Admin role for Atlassian organisation
- Cloud Application Administrator or Application Administrator for Entra ID
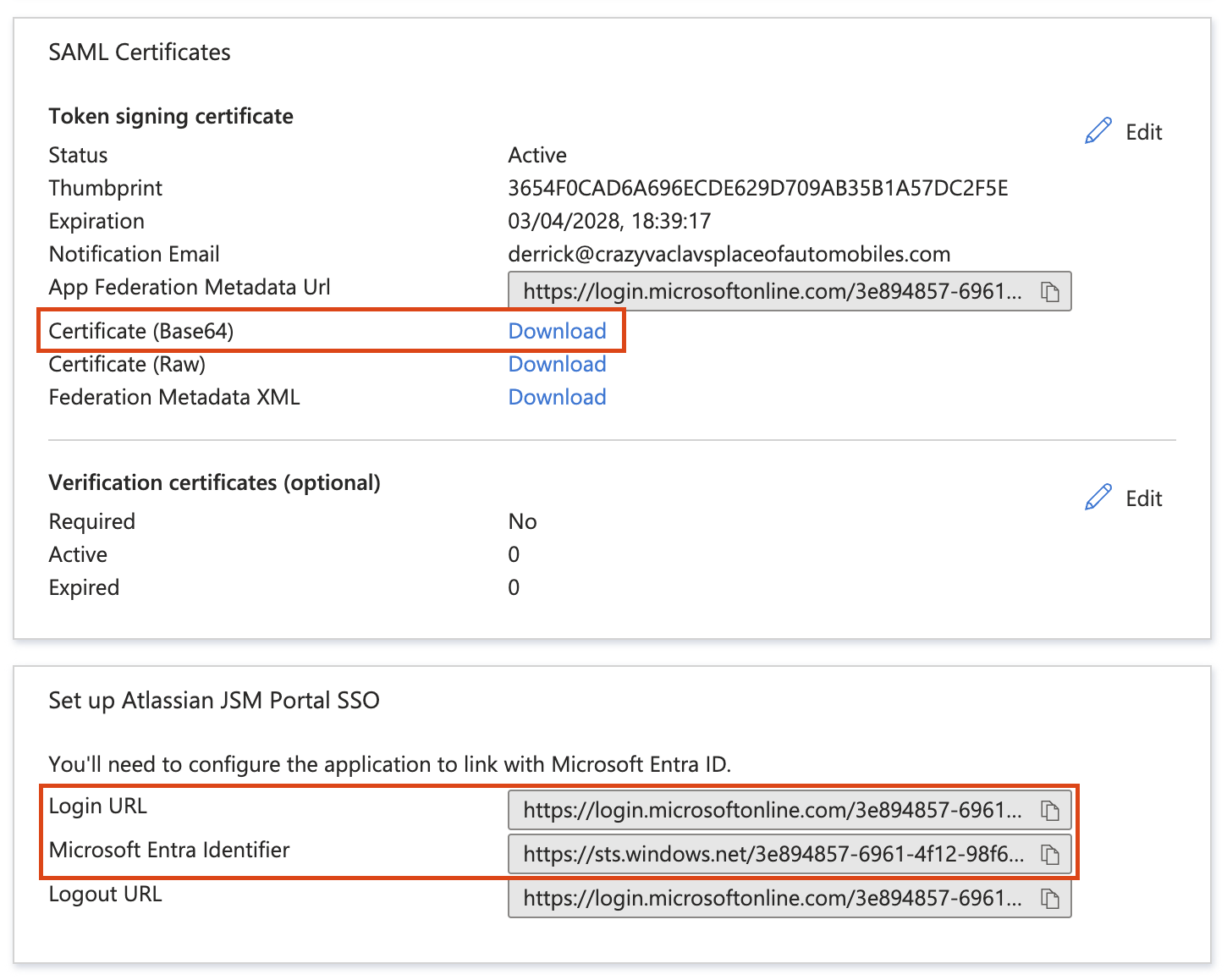
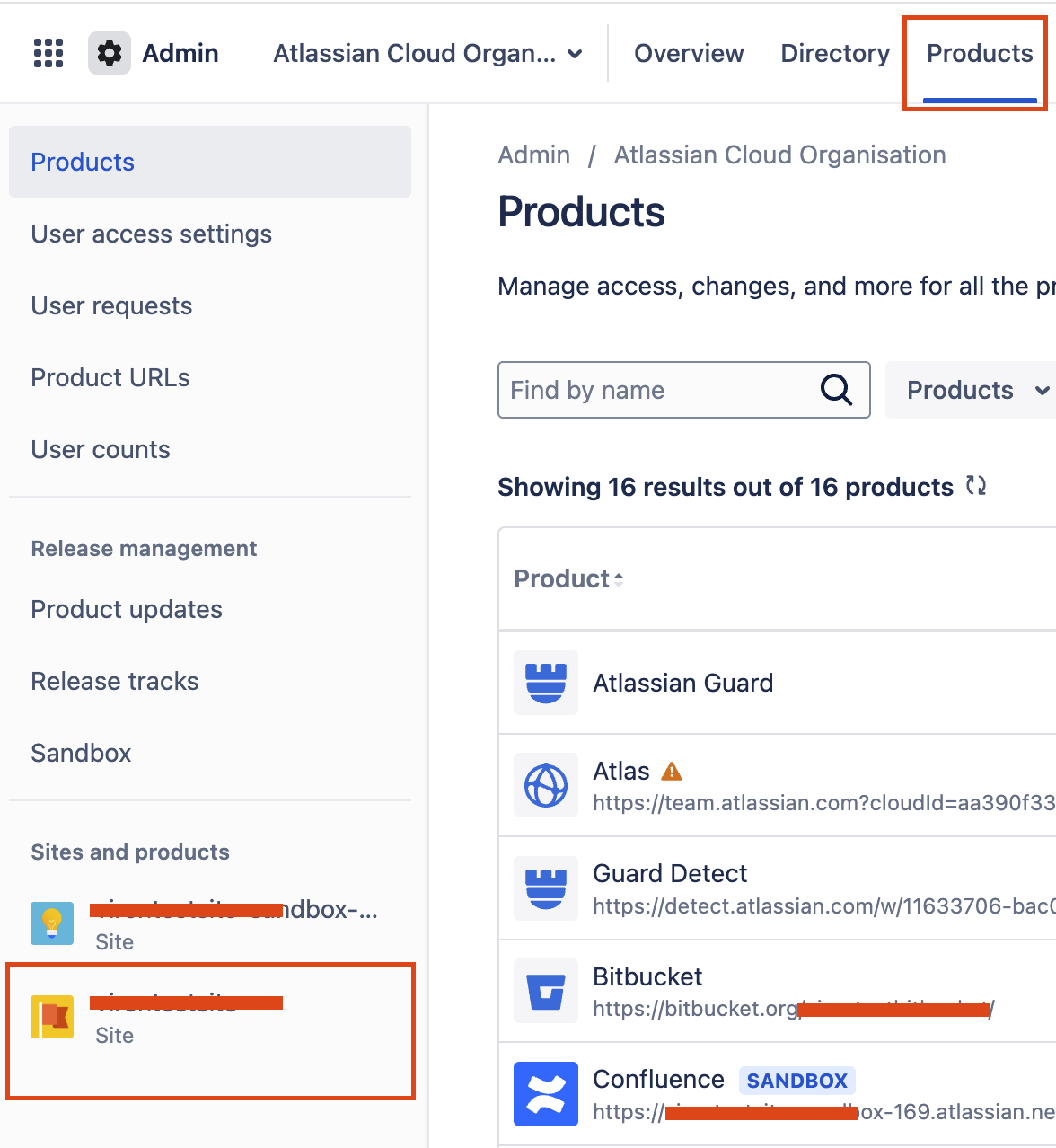
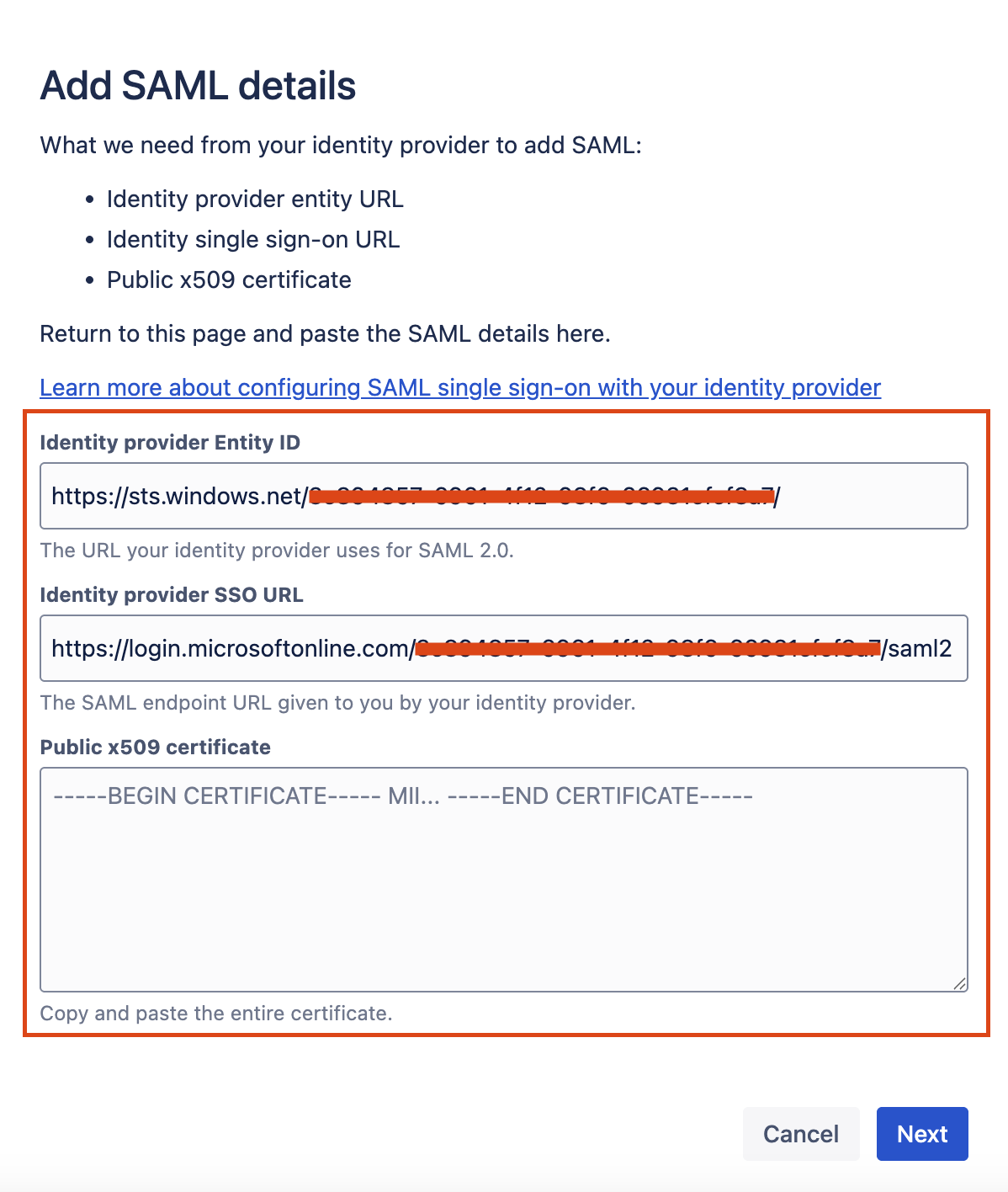
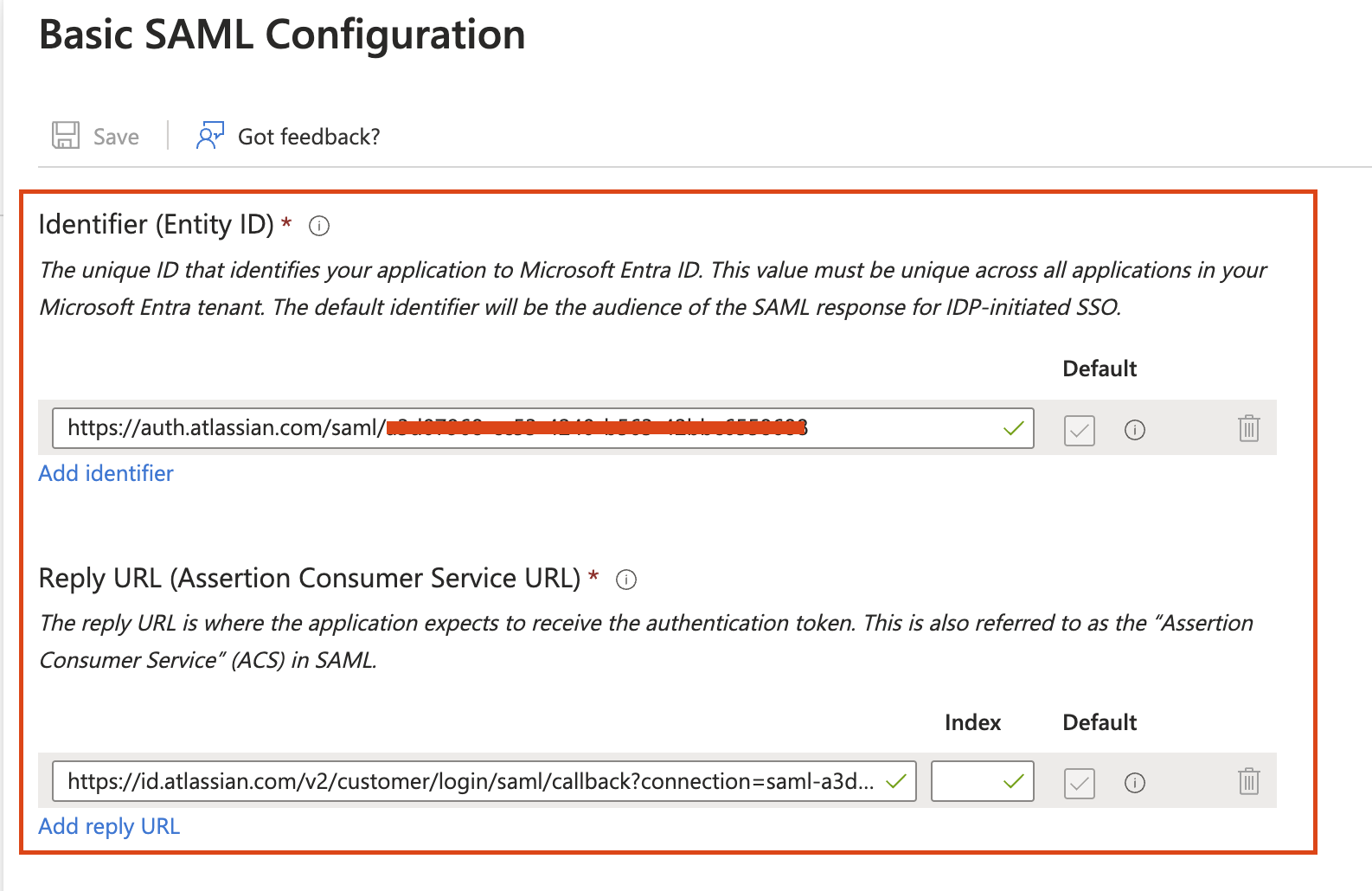
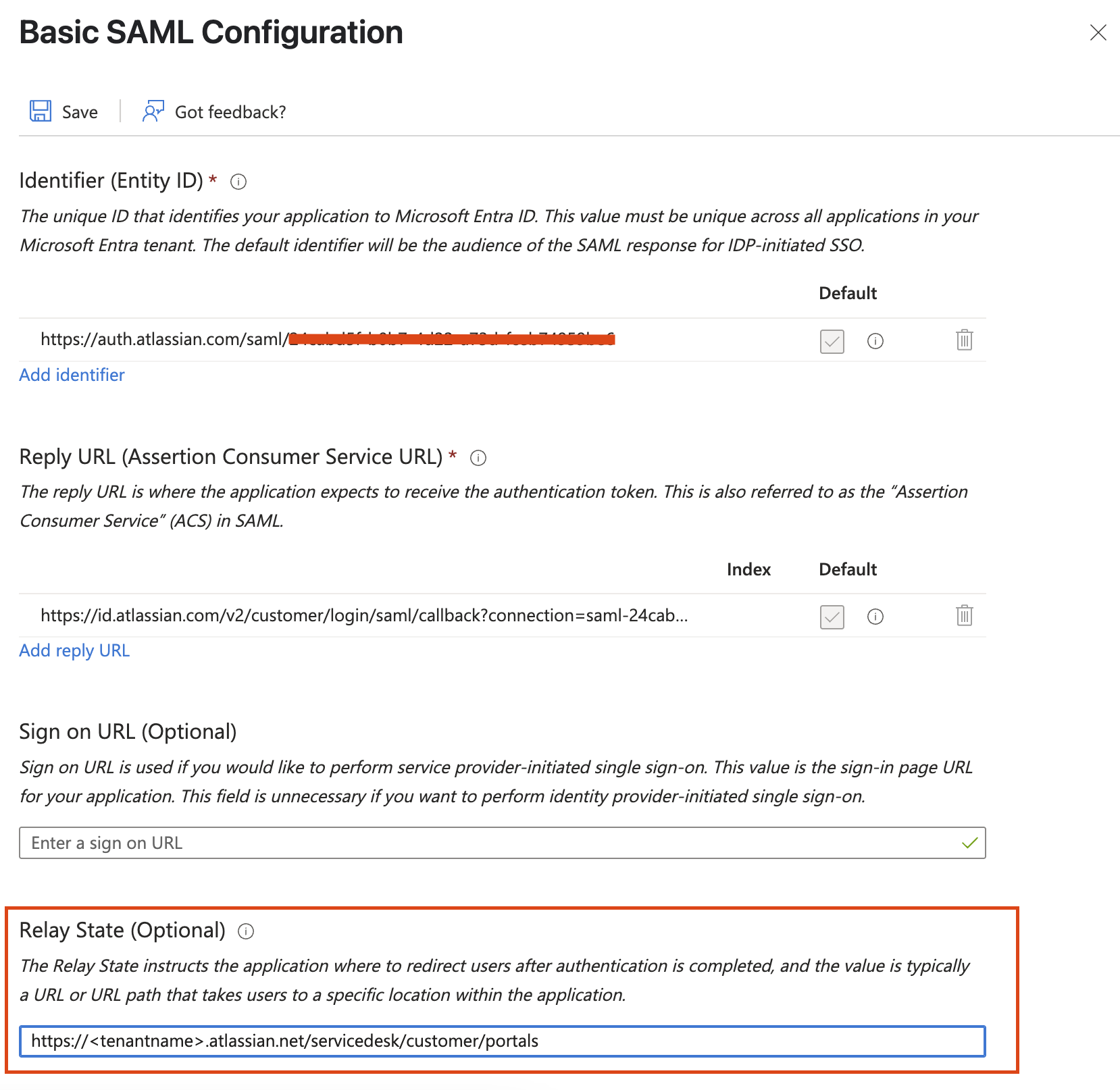
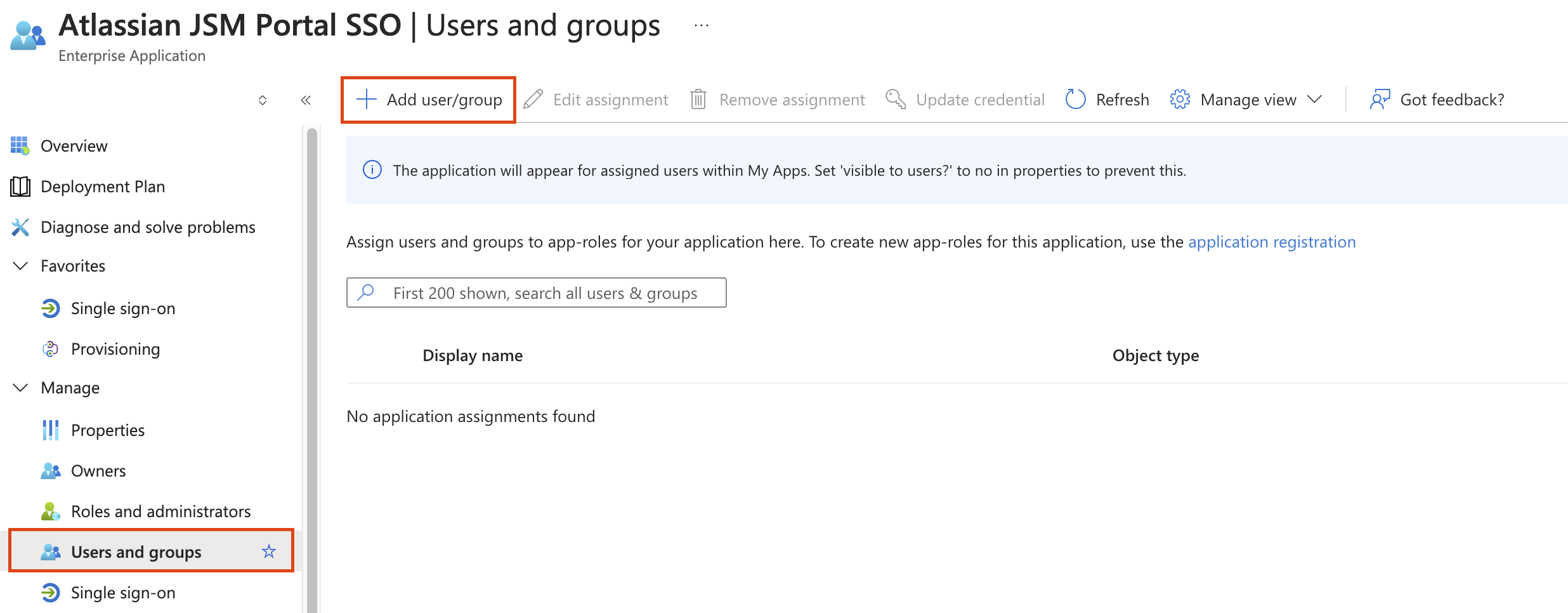
Steps to configure single sign-on
Please follow the below steps to configure the SSO with the Entra ID for JSM Portal-only customer users: